Introduction to Security Information and Event Management (SIEM)
In the thrilling world of action movies, the narrative often revolves around cunning villains who exploit security weaknesses to achieve their nefarious goals. This scenario isn't just limited to cinematic fiction; it mirrors real-world cybersecurity threats where hackers incessantly target system vulnerabilities to infiltrate networks. Just as the movie heroes stand against these adversaries, security analysts are the unsung champions in the cyber realm. Their task is monumental, yet it's compounded by the challenge of using multiple security tools that, unfortunately, do not communicate effectively with each other. This can lead to significant analyst burnout, as they manually integrate and sift through mountains of data to identify critical threats.
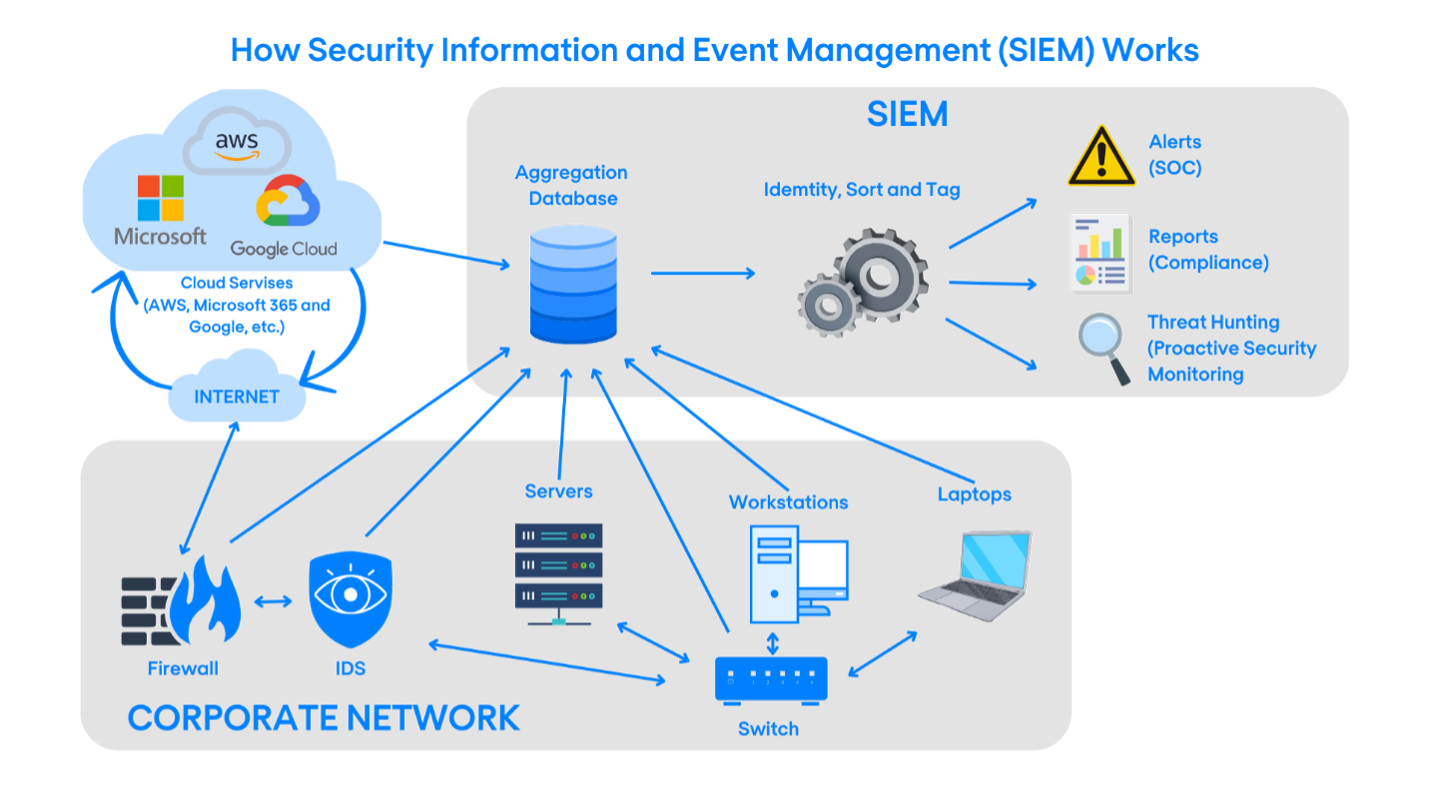
To counteract these challenges, organizations deploy Security Information and Event Management (SIEM) systems. SIEM serves as a sophisticated command center, akin to a high-tech operations hub in a spy film, where all critical data converges for real-time analysis. It aggregates and analyzes data from a myriad array of sources across the network, including logs from servers, computers, firewalls, email security tools like Proofpoint, and endpoint protection platforms like SentinelOne.
The power of SIEM lies in its ability to provide a unified view of an organization's IT security. It's designed to collect and correlate logs and alerts generated by various devices on the network, transforming this data into actionable intelligence. Think of SIEM as the central intelligence agency in an action movie, where different pieces of information are pieced together to form a coherent understanding of a potential threat. For example, if an unauthorized attempt is made to access a server, SIEM can correlate this event with an unusual login attempt detected by an endpoint protection tool and an alert from an email security tool indicating a phishing attempt. This correlation helps in painting a complete picture of a potential security breach, allowing security teams to respond more swiftly and effectively.
Moreover, modern SIEM systems are enriched with advanced technologies such as Artificial Intelligence (AI), Machine Learning (ML), and analytics. These technologies enhance the SIEM's capability to sift through and analyze massive volumes of data in real time, detecting patterns and anomalies that might indicate a security threat. This is similar to a detective in a movie using clues to uncover a larger plot. The system generates high-fidelity alerts that prioritize threats based on their severity, akin to a spy distinguishing between trivial distractions and real threats that require immediate action.
As cyber threats evolve with hackers using more sophisticated technologies, SIEM continues to be an indispensable tool for organizations. It acts like the high-tech gadgets used by movie heroes, equipping security teams with a comprehensive arsenal to defend against a spectrum of cyber assaults. SIEM integrates with User and Entity Behavior Analytics (UEBA) to analyze both normal and abnormal behavior, aiding early detection of security issues. Additionally, with Security Orchestration, Automation, and Response (SOAR), SIEM can automate responses to security incidents, reducing the manual workload of security analysts and allowing them to focus on strategic security tasks.
This advanced tool is crucial for maintaining robust security across an organization’s networks, applications, systems, and storage devices, providing a strategic advantage much like the secret weapon of a hero in an action film. Understanding the role of SIEM is vital for enhancing organizational cybersecurity, serving as the linchpin in the ongoing battle against cyber threats.
By harnessing the full capabilities of SIEM, organizations can not only defend against current threats but also anticipate and mitigate potential future vulnerabilities, ensuring a proactive security posture. For those interested in exploring how SIEM can revolutionize your security operations, ensure compliance, and boost operational efficiency, we encourage you to reach out to us for a more detailed discussion. Visit our contact page, email us at sales@MeritTC.com, or call our sales team at 832-458-1812 to request a network assessment and discover how our solutions can benefit your organization.