Cyber Threat Assessment Objectives
PURPOSE
- Identify security risks and understand corporate network usage.
- 54% of businesses had severe exploits in Q4 20181
- 14 malware variants detected per firm in Q4 20182
- 75% of traffic is expected to be encrypted by 20193
OUTCOME
- Raised awareness to gaps in current security, and user impact on network
REPORT CONTENTS
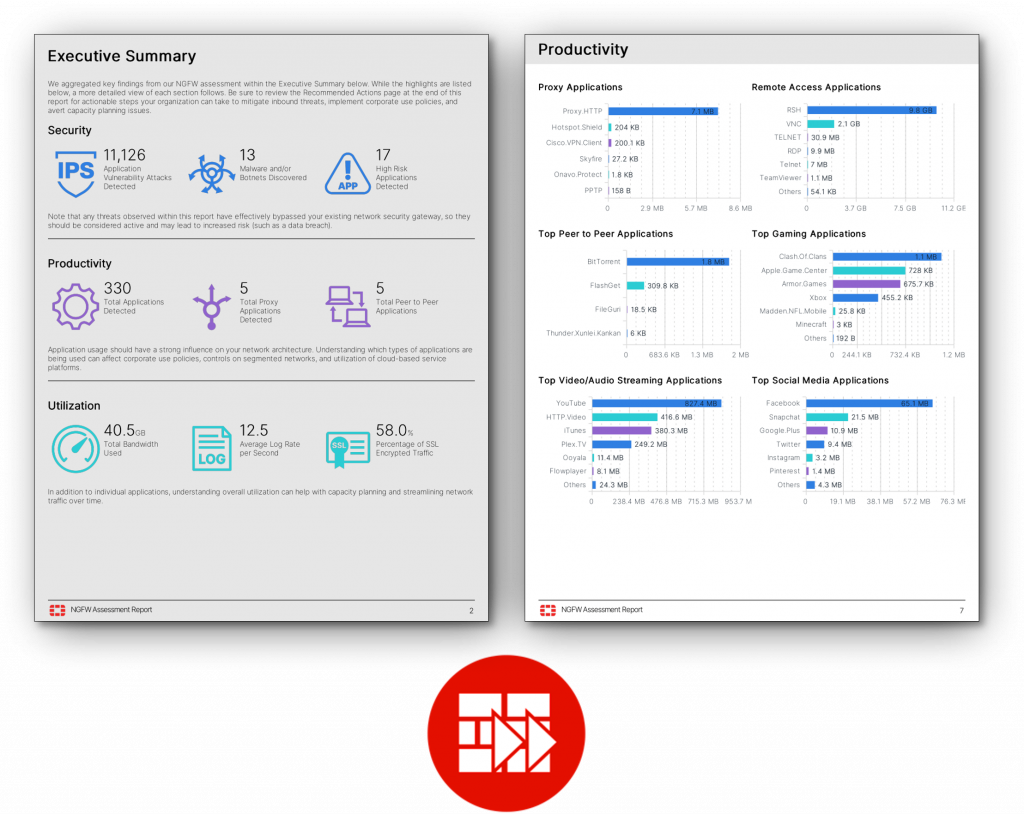
- Security | Productivity | Utilization
Included in the NGFW Assessment Report

SECURITY
- Application vulnerabilities observed
- Malware / botnet detection
- At-risk devices within the network

PRODUCTIVITY
- Application categories and cloud usage
- Peer-to-peer, proxy-app, and remote access
- Web-based applications and browsing habits

UTILIZATION
- Bandwidth analysis and top consumers
- Average log rates / sessions for sizing
- SSL utilization and encryption impact